This weekend I went to a friend's house and we talked a lot about photography, another passion of mine. So I decided to use my iTouch to show him my online portfolio:
- sorry man - he said - I have to tell you my home network name. Otherwise you won't see it available to connect.
- what do you mean? Do you hide your wireless SSID?
- Yeah, I do this for security reasons.
And yet again here we go, another old security myth: Hiding your wireless SSID makes your home network safer.
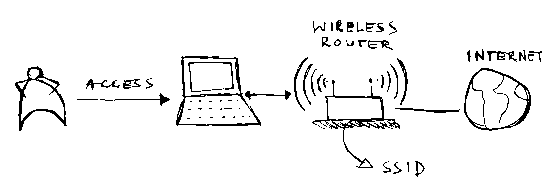
First of all, what is this ?
In your house you may have Internet access. If you have a laptop what the people normally do is to buy a router, then connect the Internet cable to the router and then the router will 'emit' the signal to the air. This will allow you to connect to your Internet from your bedroom, kitchen, talk to your mother over MSN while walking around your house etc. Everything wirelessly, as long as you can still get the signal. And for that we give a friendly name to this signal called SSID, so you know where to connect.
The thing is, everyone who has a computer with wireless connection also sees your signal.
So how to avoid them to connect to your Internet and make them surf by stealing your connection? Well, you set a password to connect to your router, so when anyone try to connect they will be asked for it.
And here we get to the point: the SSID is not a password. As a matter of fact, the SSID was designed to be public, yes. So by making it public or hidden it really does not change much the security scenario. And besides remember what all the security experts say: there is no security by obscurity. Just because it's hidden it does not mean that it is safe.
So he decided to hide the SSID. Ok. It does not matter, it is not much hidden anyway. Let's see.
The wireless network that you have at home send packages of data-to-air, some are encrypted, some are not, and inside those who are not encrypted they also contain your SSID name. Simple like that and written in plain-text.
So if I am a hacker, I could use a sniffer program to capture the packages and open up to see what's inside. A lot of them I would see crazy stuff, those are encrypted; but in some of them I would see things of the like: trying to connect to SSID name 'myhomenetwork'.
So there we go, our secret is now gone. Do you still think you're safer after that?
Can you reduce the amount of packages without encrypted information? Yes, but you can not stop them 100%, so at some point they will be sent.
Another thing to worry about. If you use Windows XP we can observe an interesting behaviour. If your SSID is hidden, but the laptop is connected to the Internet, XP still apparently keeps sending requests to join the network, continuously. And guess what? The router will reply to your requests using non-encrypted messages.
Funny thing. If we think about it what we are doing here is make our hidden network sends over and over and over again a bunch of replies with not encrypted data with your so-cool-and-hidden SSID.
Why Windows XP and Windows Vista behave like this by default? because SSIDs were, as I mentioned before, designed to be public and I my guess is that Microsoft did this to comply with some governments cyber-laws. I've heard that in some countries, like the USA, it is a crime to keep your SSID hidden and to use hidden identities and hidden networks... all that stuff. I can't confirm that, so it is a guess, but it makes sense to me.
Hiding the SSID won't hide you from the wireless world. Unfortunately people still relates hidden things with secure things.
So how to make my wireless Internet at home more secure? Use something called WPA/WPA2. That's good enough mostly the times. If you are using WEP, change to WPA2. If you are running Windows XP and you have applied all the updates, you are safe. For Windows Vista is even easier because WPA2 comes with it out-of-the-box.
See you later.
By Edge Pereira



 Here there is something interesting that I would like to share with you guys.
Here there is something interesting that I would like to share with you guys.