Another day, another big data leak. Do you have a minute? Let's talk a bit about basic security and how even the “big guys” can have it wrong.
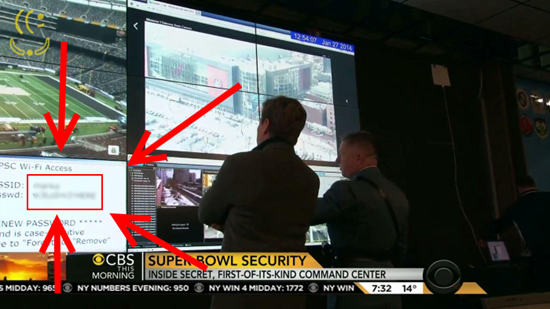
Since you're a young IT professional you hear the mantra that login credentials (username, password etc) should never be shared nor written in plain-text (Hello, TickeTek!!). So, why do we keep seeing these things in workplaces? Passwords for network shared on stick notes, handwritten in walls, displayed in big monitors for the sake of convenience…
The answer is: Unfortunately, this is quite a common practice and worst coming from bad decision making.
The Weakness Stand
According to a report from Centrify: State of Corporate Perimeter about 50% of the USA and 1/3 of UK leaders believe it is easy for someone with old passwords to login into company systems.
Even considering that most of the companies have an off-boarding process for contractors, it can take up to a week to completely sanitize access rights and passwords to all the sensitive data once handled by those individuals. One week is enough time for anyone with ill intentions to go back and hack into systems. And that isn't a rare incident.
Privileged Accounts: Free as in Free Beer
It gets worse. The report revealed that privileged accounts for systems, and network devices are being shared without any policies to protect them. 40% of U.K. IT leaders working for big companies (over 500 employees) said more than 10% of their staff have privileged access to data in some form.
This number jumps to 50% for small and mid-sized companies (less than 500 employees). Too many people with too much, unnecessary, power in their hands. We are talking about confidential and highly sensitive information kind of access. Rightly so, 62% of U.S. IT leaders believe their companies have too many privileged users. Look at this: Security Auditors guess Australian government database passwords on first attempt! That’s shocking!
Cultural Differences?
Now one thing to consider. This report was done with 200 companies in the USA and 200 in the UK. One might think that a more liberal economy would pose a bigger risk to IT security systems. Truth is, it does not. The overall pattern is consistent across all groups in both countries. For example, around 50% percent of all companies involved in the study confirmed that their companies had a data breach. And the bad guys are there for the taking like sharks.
A Backup Always Work, The Restore Is What Fails
Almost all companies have some sort of identity keys in place but nearly half of them have monitoring, auditing or privileged identity management in place. Quite surprising, 1/3 of these companies don't have trained employees to respond to a data breach or how the accounts are used. They are simply given to folks and trusted they will do good with them. No wonder so many breaches happens.
The Disaster is a Decision
Often times we hear that a disaster is a series of small events that lead to a big event. It is very surprising that experienced senior managers and leaders on this day and age are still following bad decision making frameworks, yet admitting they do need to do a better job with their data. The quote "When a data leak happens, it is probably your fault" is becoming more alive than ever.