TickeTek is a great site. Actually, I love all the online booking capability industry. These guys apply a lot of cool stuff over the internet to make our lives easier when booking tickets for events. No more queuing to get to that place and worrying about where one will be seated. (unless you’re an iFan)

And because they deal with personal details and personal information, they should be extra careful to make sure data don’t get leaked for criminal purposes. Which brings us to the reason I am writing this post.
The other day I went on to book tickets for my family so we all could go see the Australian football competition. We picked the Brisbane Roar vs. Central Coast Mariners game. It has been a while since I bought my last tickets and I forgot the site password.
No worries, just click the option to remind the password, right? so, I did that and this is what I’ve got in my email.
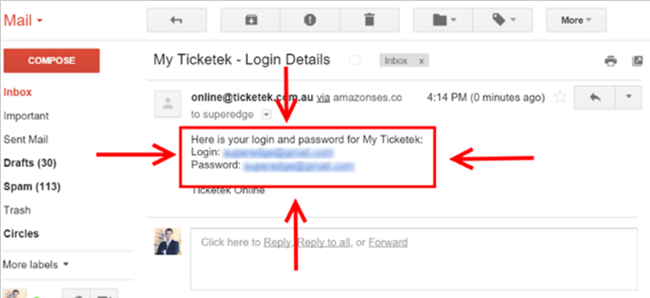
Yep. They sent me my username and my password, in plain text to my email. To the unaware or naive mind, this doesn’t look too bad, actually some people think this is very cool, so you don’t think about a new password. Just use this one, right?
Here’s the problem: If they are sending me my password then…
- They are storing my password as it is or;
- They are storing my password in a way that it can be scrambled/descrambled
Either way, they are storing my password somewhere. And that’s not great! Room for improvement here….
Why is this a Problem?
There are a lot of problems with this, but I’ll nail it down to 2 points:
- Email is not a safe environment. There are hundreds of types of attacks that can be done on emails. The email protocol itself is not encrypted.
- Easy as copy/paste. If someone get hold of my email account, they can go and search for the text “password” and voila…there it is for the taking. And there is no need for hacking to be involved. Just need to leave your browser accessible for a few minutes while you go do something else and you’re done. The options go from someone lurking behind your back and writing down the password, until virus that take screenshots of your computer.
- Multiplication of the weakness. Now your password is stored: at your place, at TickeTek and now in your email server. Like it or not, every time that email gets forwarded it increases the chances of someone getting hold of it.
So, here TickeTek is telling me that “hey, if you forget your password don’t worry, we are storing it for you in plain-text, or using a reversible encryption process to get it for you”. This is a big no-no! This is a sign of poor thought out security here.
Another problem is that if a hacker gets a very limited, very restricted access to the system…let’s say, “read-only” kind of access, he/she still can read the password and from there empower themselves to a higher ground of disaster. This is not unheard of. If you don’t believe me ask the folks at:
All these people said they used secure procedures to safeguard user’s details, yet when they were hacked it was all exposed they did not go through the steps to make sure it was secure enough. The sad conclusion here: This is still a very common vulnerability even among big companies. 

General rule: Nobody, nobody except you, should know your password.
Who Owns My Data?
Ok, further in the process. Now I have the right username and password, then I proceed to buy the tickets. Because I once bought tickets with the site, they stored my credit card details. Now you see the danger brewing…
Imagine if someone grabs my password. Because the site stores my credit details, now the hacker have my credit card. The party is getting better.

The Privacy Policy
The publication BusinessWeek did a report on internet privacy where the results show that the majority of internet users are worried about how their personal information can be used. From a customer respect perspective is it always good to have a privacy policy. A privacy policy’s objective is to disclose, to inform people (visitors/customers). TickeTek is doing the right thing here. They also have a privacy policy. That shows they care for how the information is handled and they have guidelines. Great job here TickeTek.

However, by looking at the policy (something I am sure a large parcel of the visitors don’t do) we see statements like this

I would say that text is missing some points because as you could see they store my password. But maybe here’s the reason why. Apparently the personal information collected is stored outside TickeTek on a 3rd party vendor database.

Which can get even more complicated. This increases the surface for attack. Here are some possible attack vectors:
- What if such database is backed up by yet another external company
- What if the operating system from these companies are not fully patched against security risks
- What if there are weak points in any other hardware or software firewall involved
- What if a given user that have access to this database get a virus that could exploit the data
- What if this database, for whatever reason, ends up in a computer, laptop, removable media and it gets stolen
- What if a frustrated employee, not related to Ticketek at all, decides to "hit back"
All these are plausible scenarios and require appropriate mitigation strategies in place. In-depth security: every layer in the system needs to be hardened individually.
In short, here’s the diagram explaining this. Look at the attack vectors in red:

So now, there you go, your password is stored in yet another place, a 3rd party company. And again, to bring up the point of the security vulnerability: This 3rd party company might have a team of IT professionals that can handle the data stored. So now your password is stored:
- In your email server
- In anyone’s email server if you forward the message in anyway
- In your ISP
- In your laptop or mobile
- In someone’s else company …
So the threat model now has additional attack points, because now you are involving more parties. And again: the password it is still stored either in plain-text or in a way that it can be deciphered. Regardless the way you want to look at it, this is a bad practice….but salvation is at arms length and it is not complicated at all to fix !!
Fixing This: How Should Passwords Be Stored?
Well, ideally you wouldn’t want to store a password. Let’s take a step back and see the purpose this: Authentication. If we stop to think about it, we don’t need to check if the password matches, we need to check if the password is right! And there are several ways to do this, one way is to generate something called “hash”. A hash is a code generated using your password as initial value and an additional value called “salt” which is random and individual per password. That code is always unique and that’s the value you should store. I like the analogy that the hash is like putting meat through a grinder. Anyone can manipulate the meat afterwards but there is no way you can restore the meat to the original state. Likewise, you can always verify the hash generated based on the password the user provides in the website, but there is no way to process it and to revert the password back.
And because nobody knows the user password, no email can be sent to them with a plain-text password. Instead, an email will be sent with instructions to set a new password, which is not only a good security practice but also forces the user to recycle an old password.
It is All About Reducing the Surface for Attack
Techniques like this will not avoid a website from being attacked. If you were patient enough to read up to here (thanks for that, I really appreciate it!  ) you see that all we want to do is reduce the surface for attack and minimize the damage. Adding enough security measures in place to make sure that even if an attacker can get hold of this data, the potential for damage is minimized.
) you see that all we want to do is reduce the surface for attack and minimize the damage. Adding enough security measures in place to make sure that even if an attacker can get hold of this data, the potential for damage is minimized.
One More Thing Before You Go
I wanted to point out also 2 cool things the website is actually doing very well. See this image below, this is me sniffing all the internet traffic between my computer and TickeTek website during the credit card processing. Everything is using SSL/HTTPS, which means all the communications are encrypted. Good job!

Also TickeTek has a Privacy Officer, which is pretty cool if you ask me. If you’re a customer and have any concerns about your data and how it is being handled by them, just contact these folks and they will address your concerns. Good job again !!

On a final note, all this thing about sending passwords in plain-text via email is a big security issue because it comes from a weak security stance, which then projects an image of “hey, other places might not be using the best security practices”; however this fix is extremely common and, I dare to say, is a bread-and-butter of any decent programmer.
I really hope they fix this soon! By the way, I did send this post to their Privacy Officer.