A blog on Office 365 DLP, SharePoint, Data Protection, Privacy and Compliance in the cloud.
I Am Presenting at the Azure Smorgasbord in December 2015
How does your day look like on December 9th 2015?
Come join me a Microsoft to discuss and share ideas about IoT, Azure and Office 365 in Australia.
Session Name: “IoT - The Invasion of Australia”
Abstract: “Five million new IoT devices will come online every day in 2016. Do you want a piece of this 50 billion dollar cake? Join Edge Pereira to discuss a use case of IoT in Australia and why we are in a prime position to lead the world in this area.”
Where Can I Find the Presentation Slides?
Hour of Code 2015. I am Volunteer. Again.
Once again this year I am volunteering time for the Hour of Code. And proud of it. Listen what Bill Gates, Mark Zuckerberg, Jack Dorsey and others have to say about this event.
What is the Hour of Code?
Launched in 2013, Code.org is a non-profit dedicated to expanding access to computer science, and increasing participation by women and underrepresented students. The vision is that every student in every school should have the opportunity to learn computer science. Code.org believes that computer science should be part of core curriculum, alongside other courses such as biology, chemistry or algebra.
When It Happens?
Volunteers from all over the world help local teachers and their classes during the Computer Science Education Week that happens every year in December. This year it will be from December 7th to 13th.
How Can You Help?
We have this year 13.000 requests from teachers from all over the world, but only 4.000 volunteers. We need volunteers to help with the activities and help the teachers. Here are a few things you can do also to get involved:
- Recruit co-workers to volunteer: Blog, share, tell your friends and co-workers about the Hour of Code and ask them to sign up as a volunteer.
- If you know someone who’s a volunteer, connect them with people who wants to setup Hour of Code parties.
I Want to be a Volunteer. What Do I Need to Do?
To get a better idea about what your volunteer experience will be like, have a look at this guide. There's also some extra tips about how you can get your employer and community involved with the Hour of Code.
If you know anyone needing help with it, feel free to connect with me. Remember: I am a volunteer!
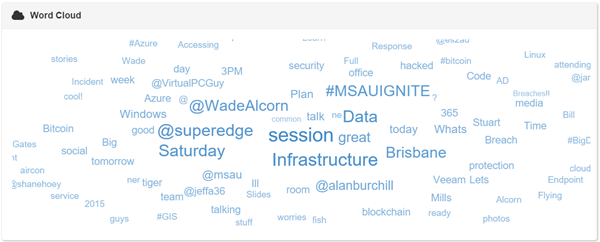
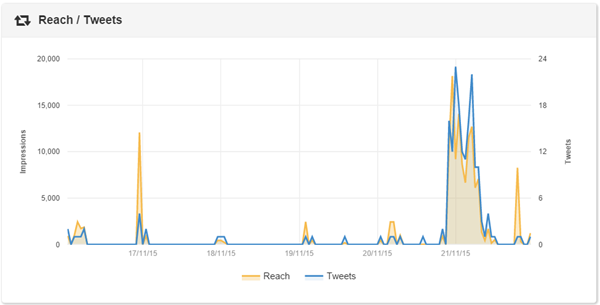
Infrastructure Saturday 2015 Social Media Stats #infrasat
We’ve just done another successful Infrastructure Saturday event. It takes a lot of time and passion to setup personal time aside and to organize such an event. This is an annual event totally built and sponsored by the community, so the people you find there (attending, organizing or presenting) are 100% committed to the cause. Big shout for the guys organizing: Alan Burchill and Shane Hoey
Below are some of the social media stats collected during the last week up to the event day. This years top contributors were: JustBroady, superedge, david_obrien, pzerger, cloudtidings, bneusergroup, alanburchill, twalex2, blkchninstitute, reecestewart4
If you’ve been to the sessions, thank you very much. I hoped you enjoyed and see you next year.
Top Links about the #infrasat Infrastructure Saturday 2015 Event
- https://www.flickr.com/photos/alborath/albums/72157660731316669
- https://twitter.com/DigitalGlobe/status/667834517428682752
- https://code.visualstudio.com
- http://www.infrastructuresaturday.com/
- http://www.superedge.net/2015/11/ethereum-blockchain-service-bitcoin.html
- https://lnkd.in/b_GeEXZ
- https://lnkd.in/bk9tVcN
- https://doc.co/75WgEz
- http://www.linkedin.com/pulse/want-increase-privacy-protection-your-cloud-data-worries-edge-pereira
- http://www.infrastructuresaturday.com
- http://infrastructuresaturday.org
- https://lnkd.in/buajN7R
- https://lnkd.in/bkYJbY4
- https://lnkd.in/bBgh534
- http://www.superedge.net/2015/11/infrastructure-saturday-2015-australia.html
- https://lnkd.in/bhp3pyZ
Azure DevTest Labs Now in Preview
Busy week for Microsoft Azure. Another feature comes in preview today: Azure DevTest Labs
What it is ?
Azure DevTest Labs gives developers on-demand self-service for Azure-based test environments. With DevTest Labs developers can:
- Quickly provision development and test environments.
- Minimize waste with quotas and policy enforcement.
- Set automated shutdowns to minimize costs.
- Create a VM in a few clicks with reusable templates.
- Get going quickly using VMs from pre-created pools.
- Build within Windows and Linux environments.
- Integrate directly with your preferred CI tool, IDE, or automated release pipeline.
A really cool feature is that the Dev VMs can be saved as templates and reused across organizational teams of developers.
How Much it Costs?
Azure DevTest Labs is a free service. However, you will be charged for other Azure resources that are created in the Lab. For example, you will be charged for the virtual machines that are created in the DevTest Labs per our virtual machine.
See this new product here at the Azure DevTest Labs webpage
Azure Disk Encryption Now Available
Brand new feature deployed today on Microsoft Azure as preview: Disk Encryption
About Azure Disk Encryption
Azure Disk Encryption for virtual machines (VMs) is the answer to many organizations that could not have VMs running in the cloud mainly due to security and legislation compliance requirements.
What it Does?
What this technology does it to encrypt the VM disks, including boot and data disks, with keys and policies which are controlled in the Azure Key Vault.
It Works for non-Windows Systems
Disk Encryption for VMs works for both Linux and Windows operating systems. It also uses Key Vault to safeguard, manage, and audit the use of disk encryption keys. All the data in your VM disks is encrypted at rest using industry-standard encryption technology in your Azure Storage accounts.
What Encryption is Used?
Windows VMs uses BitLocker and the Linux VMs are using dm-crypt
How Much it Costs?
This is at no charge. Gratis! The reason for that is because this is brand new and still in preview mode. Microsoft is expected to start charging for it in some way when the product becomes live. Meanwhile it is a great opportunity for you to start playing around with it and testing your systems.
I’m Speaking at the Infrastructure Saturday 2015 Australia
Once again I am honoured to be part of the Infrastructure Saturday event in Australia. This is such a great opportunity to connect with the local IT community and talk about tech and experiences with a local flavour and feel.
Session Details
- Title: “When a data breach happens, what’s your plan ?”
- Abstract: “Ashley Madison, Sony, Kapersky Labs, LastPass, CentreLink, G20 event in Brisbane…What do they all have in common? They were victims of data breaches. And as you probably know by now, some were handled better than others. In this session we will talk about strategies, from mitigation to handling, used when a data breach happens (not “if”) and what controls do we have if you are using Office 365.”
- Local: Microsoft Offices, George St, 4000, Brisbane, Australia
Where Are the Slides?
Looking forward to talk about this topic!! Below are some of the art done to promote my session. Loved the work
List of the Most Common Passwords
Ah the joys of working on a specialized cloud security company. This list got to my hands and I am quickly circulating them with you. These guys do a lot of pen testing, network and cloud vulnerability assessment, cloud assurance etc.
Is any of these your current password somewhere? I hope not!
Microsoft to Store Data in Germany. Make it Harder for Foreign Authorities. Safe Harbour Lesson #1.
Here’s a way to increase your data protection from US government access: Store it in Germany!
As you probably know, in October 2015 the European Court of Justice declared invalid a "Safe Harbor" agreement between the European Union and the U.S. that allowed Facebook and other firms to transfer data in huge quantities to their servers in the U.S.
The court threw this deal in the bin because it was worried about "mass indiscriminate surveillance and interception" of personal data by the U.S. authorities.
And that’s what’s Microsoft is proposing: to make it harder for Government authorities to put their hands in people’s data.
Why Germany?
After the whole saga between Microsoft vs. USA Justice Department, European consumers, rights groups and lawmakers have expressed concern about what U.S.-based companies share with American authorities.
The European Union has very rigorous rules to protect data, and Germany's regulations are considered especially strict. Besides that EU authorities have been clamping down on data protection in recent months over concerns about mass spying by U.S. intelligence services. Especially after the revelations made by former NSA contractor Edward Snowden that the U.S. spied on German officials, including Chancellor Angela Merkel, angered Berlin.
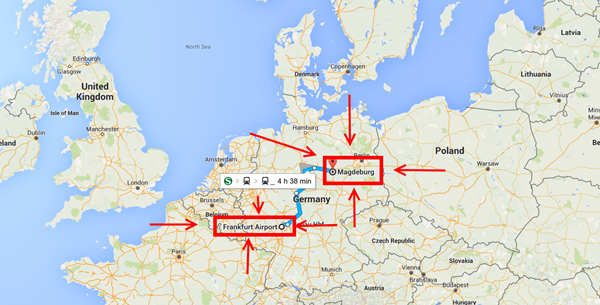
Where Will the Datacenters be Located in Germany?
They will be in Magdeburg and Frankfurt. These new datacenters will maintain the same level of expectations , security, service and quality standards as all Microsoft datacenters globally. The services offered will abide by the Microsoft trusted cloud principles of security, privacy, control, compliance and transparency, as well as consistency with Microsoft’s global cloud services.
The reason for 2 datacenters is to ensure business continuity. Also their data will be exchanged through a private network to ensure data resides in Germany even in transit.
What is Planned to be Stored in Germany?
As part of this big initiative, Office 365 customers will soon be able to choose to store all data from the following products in Germany:
- Azure,
- Office 365 and
- Dynamics CRM Online
Who Will Oversee this Data?
Deutsche Telekom will be the assigned data trustee and will control and oversee access to all customer data.
What is a Data Trustee?
Data trustee is an entity that will handle data on your behalf. In this case, it will be a company called T-Systems, which is a subsidiary of Deutsche Telekom. It means that Microsoft will not be able to access this data without the permission of either:
- customers or
- the data trustee itself
and if permission is granted by the data trustee, will only do so under its supervision.
This is ground-breaking stuff. Never done it before in Europe and after the repercussion of the Safe Harbour case, this service is expected to grow rapidly.
What are the Impacts on Compliance for Customers?
These new cloud services in Germany will specifically address organizations and enterprises operating in data-sensitive areas such as the public, financial or health sector. The immediate effect on this is positive: Now you can even choose the datacenter within the EU jurisdiction which will translate in a better granularity of controls.
We are talking about the German Government which traditionally have a very high level of data handling regulations and security by default. As a matter of fact, Germany is one of the leaders in this quadrant. Together with Customer Lockbox, customers will be able to view how and where data is processed.
Will this Avoid the US Authorities to Access my Data?
Honestly, No. Any government that requires access to data stored in the cloud, regardless of the provider (Microsoft, AWS, Google etc) will get this access. In a fight between governments and private companies, governments always win.
However this move will make it increasingly harder for governments to have this access. And that’s the main goal here. It is not to block the access, but to put stronger controls around data access by other people except the data owner.
This move will be likely followed by Amazon and Google very soon.
Sounds Great! When Can I Move my Data to Germany?
There is a LOT of ground work to cover. Involving auditing, certifications, and buildings construction. Microsoft is releasing this information now to calm-down the nerves of some big customers. The expected timeline for availability will be around the 2nd semester of 2016
CheckList to Buy an Used iPhone
I am in the market for a new phone. Got tired of my Windows Phone, which I gave so much love for years but unfortunately the market didn’t care for it. Windows Phone is like a beautiful princess locked in a castle that noone knows where it is.
I am going for an iPhone. You can’t beat its app store. Nowadays people don’t buy phones, they buy the app store.
I am thinking about buying a 2nd-hand device so I listed a few things to check when I found one and I am sharing these tips here with you. Hope it helps you as well if you’re in similar situation.
Here are my 9 checks to perform a good smoke-test on the device you want to buy:
- Check for Warranty and Support Status
- Check the iPhone Activation Lock Status
- Examine the Device
- Test the Display
- Access the Internet over Wi-Fi and Cell Network
- Make a Call and Send a Text to a Friend
- Take a Picture and Make a Movie
- Check the Battery
- Disassociate the Device from iCloud
And now let’s go into more details on how to check them.
1) Check for Warranty and Support Status
If the phone you’re buying is sold as “under warranty”, make sure it is. Enter the iPhone serial number into the Apple’s site to see the report. You can check this here.
2) Check the iPhone Activation Lock Status
Before transferring ownership of an iPhone make sure the Activation Lock has been disabled and the device is ready for the next user. This also applies for iPad, iPods and Apple Watches. You can check this here.
Note: Once an IMEI is blocked, let’s say due to theft or lost device, it cannot be undone. It means the device has officially become a brick. With no use for noone except the recycling company. So if the IMEI is locked here, don’t bother testing anything else…actually, you CAN report it to the police.
3) Examine the Device
Scratches, chipped glass, dock connector. Then plug the phone in a charger to make sure it will take a charge. Listen to music through the headphones. Use the headphone’s controls to navigate music and volume.
4) Test the Display
This is tricky as well. Make sure you are in a place with good natural light when inspecting the phone screen. Visit this website iPhone Dead Pixel Tester to test for dead pixels. Make sure the screen displays a solid colour and it does not have any stuck pixels that won’t go away.
5) Access the Internet over Wi-Fi and Cell Network
Go and browse places like news or weather sites because they have tend to have small local caches.
6) Make a Call and Send a Text to a Friend
This is to make sure the phone perform trivial tasks as expected. During the call, put the volume up and down. Pay attention how you communicate with your friend and check if the call behaves as expected.
7) Take a Picture and Make a Movie
Make sure the photo does not look weird, too dark or too bright or have fuzzy spots.
8) Check the Battery
Go to Settings/General/Usage and check the time when the device had the last full charge. This is a bit tricky, but once you have the phone use it as much as you can and see if you are getting the battery duration expected.
9) Disassociate the Device from iCloud
Hopefully you won’t be buying a stolen iPhone so make sure the current owner disassociates the device from the iCloud account otherwise you won’t be able to login using your credentials and activate your new phone. See how to do this here.
If you find out later that the previous owner did not disassociated it properly or he/she doesn’t know how to do it, ask him/her to go to iCloud, login and remove the device from their account. They can do this by going here.
Ethereum Blockchain as a Service Now Available on Microsoft Azure
Microsoft and ConsenSys are partnering to offer Ethereum Blockchain as a Service (EBaaS) on Microsoft Azure so Enterprise clients and developers can have a single click cloud based blockchain developer environment. The initial offering contains two tools that allow for rapid development of SmartContract based applications:
- Ether.Camp - An integrated developer environment, and
- BlockApps - a private, semi-private Ethereum blockchain environment, can deploy into the public Ethereum environment.
What is Ethereum?
If you’re not following closely the whole movement started with BitCoin, have a look at this video.
Why Ethereum?
The Enterprise Partner Group at Microsoft is on the front lines with some of our largest customers. Everyone, particularly Financial Services, is interested in Blockchain technology. While a platform like Bitcoin has many great uses specifically as a Cryptocurrency, Ethereum provides the flexibility and extensibility many of our customers were looking for.
In Financial Services particularly, Blockchain is a major disruptor to some of their core businesses, and FinTech companies are driving innovation in this space. Ethereum is open, flexible can be customized to meet our customer’s needs allowing them to innovate and provide new services and distributed applications or Đapps.
Ethereum enables SmartContracts and Distributed Applications (ĐApps) to be built, potentially cutting out the middleman in many industry scenarios streamlining processes like settlement. But that is just scratching the surface of what can be done when you mix the cryptographic security and reliability of the Blockchain with a Turing complete programming language included in Ethereum, we can’t really image what our customers and partners will build.
‘'Ethereum Blockchain as a Service” provided by Microsoft Azure financial services customers and partners to play, learn, and fail fast at a low cost in a ready-made dev/test/production environment. “
It will allow them to create private, public and consortium based Blockchain environments using industry leading frameworks very quickly, distributing their Blockchain products with Azure’s World Wide distributed (private) platform.
That makes Azure a great Dev/Test/Production Environment for Blockchain applications. Surrounding capabilities like Cortana Analytics (machine learning), Power BI, Azure Active Directory, Office 365 and CRMOL can be integrated into apps launching a new generation of decentralized cross platform applications.
How to Try Ethereum?
It is available as an Azure VM Template. It means you need to spin up an Azure VM with the Ethereum template loaded. The virtual machine main system is Ubuntu, and it will contain a Go Ethereum client and a Genesys block. Also this template is available on GitHub, you can get it here.
Deploying with PowerShell
You will need Azure PowerShell to perform the deployment. You can install Azure PowerShell from here.
Switch-AzureMode AzureResourceManager
New-AzureResourceGroupDeployment -Name <deployment-name> -ResourceGroupName <resource-group-name> -TemplateUri https://raw.githubusercontent.com/azure/azure-quickstart-templates/master/go-ethereum-on-ubuntu/azuredeploy.json
All this is a pretty straight forward process, you will need to specify:
- Azure Storage Account Name
- DNS Name (it must be unique since it will be referenced by a public IP)
- Administrator name and password
- Size of the VM
- Location of the VM anywhere on the several Azure datacenters around the globe.
Read more about this exciting announcement here.
Western Australia Government Agencies Security Flaws
That’s appalling news. The Western Australian Office of the Auditor General engaged and was able to break into 2 Australian government networks. Worse, in the very first attempt! Both networks were using the login “admin” and password “password”. No joking here!
The Auditing team managed to download thousands of highly confidential documents into an USB drive.
And then they came back a week later…
And then they used the same login and password, and downloaded more stuff…Nobody noticed anything. No alerts, no monitoring, no defensive measures. IT team, hello?
But Wait, It Gets Worse…
Check these findings:
- Dozens of database administrator accounts using default passwords and usernames that had never been changed.
- Several database accounts with passwords as: “test”, “password1” and “sqladmin”.
- A database administrator account using password ‘DBA’.
- Other administrator passwords had not been changed for over a decade. Leaving access to people who might have left the organization still intact.
- A database server was being administered using 17 highly privileged accounts for which the passwords had never been changed!
- All 13 Production databases were hacked. None of them had back-ups encrypted. All there for the taking.
- At least one database server had never been patched.
- Unexplained misconfigurations in at least two of the agency databases with opened backdoors.
The Full Story
The Office of the Auditor General compiled a damning report about the atrocious state of the security in WA into a report, you can see it here. This is stuff of movies
Office 365 E5, Cloud PBX, PSTN Calling : Is Microsoft Becoming a Telephone Company?
Disclaimer: All this information is as of November 5th 2015. Make sure to remember that when reading in the future.
The new Office 365 E5 plan will include:
- Skype for Business with support for features including Cloud PBX and Meeting Broadcast;
- Analytics features with Power BI Pro
- Delve Organizational Analytics;
- New advanced security features
- Customer Lockbox, Data Loss Protection (DLP) and Safe Attachments
With this Microsoft’s goal is to expand the Office 365 market opportunity by more than $50 billion.
So the natural question is….
Is Microsoft Turning (also) into a Telephone Company?
Yes, absolutely they are. To make all these cloud PBX things to work they will be able to issue and manage individual telephone numbers for your business, which came to me as a surprise, and it is part of the new voice services that are coming in to Office 365. Not only this but if you have your own telephone number with a traditional telephone service, you can port your number to Microsoft. The new kids on the block are called: Cloud PBX and PSTN Calling.
How the Office 365 Plans Look Now?
Here you can see the new look of the Office 365 E plans and prices.
What About Customers Already on Office 365 E4 Plan?
Office 365 E4 will be phased-out and customers who are still interested in on-premise voice services can buy additional CAL subscriptions.
What is Cloud PBX?
Cloud PBX is your call control from the cloud. See this as a service that enables to control where the calls are going, but that's just one component. In order to allow a connection between an actual telephone network, a calling plan is needed. Customers can then either chose to:
- Have their call control in the cloud and route down to on premise and then call with one of the existing providers or
- They can choose to contract Microsoft Cloud Telephony services and connect their calls from the cloud.
What is PSTN Conferencing?
PSTN Conferencing Is the ability to be able to dial-in to conference meetings. Microsoft will be able to provide customers with actual real telephone numbers to call. As a trivia bonus, this is the same service used during the last Olympics for conferencing. It has initially a “limit” of 10.000 people connected to the same conference but according to Microsoft really this number is “in theory”. There is no limit except whatever is provided by the infrastructure. This service is provided by PSTN Calling
Will PSTN conferencing Be Available as Add-on for Skype For Business Subscription Plans and E3?
All services existing on the new E5 are already available as individual add-ons to E3 customers, assuming the pre-requisites are there. For example, you won't be able to add PSTN calling if you don’t have cloud PBX service first, obviously. Any of the services available in E5 can be purchased individually. Dollar for dollar, for bigger deployments the best value will be go all the way to E5 instead of keeping E3 and adding individual add-ons.
For Hybrid Cloud PBX Scenarios, If a Customer Wants to Buy E5 and Wants to Integrate with Their Own PBX, How Easy Would That Be?
Hum…easy? Yes and no. At the moment, there is no easy answer for that. At this stage what we can confirm is that at least currently there is technology to deploy that sort of integration with existing PBX systems and take advantage of Cloud PBX services.
Having said that, if the question is not about integrating with current PBX systems but instead you just want to take advantage of your own existing telephone connectivity to your current provider, that's a much simpler proposition. This will require a small number of small virtual machines acting as gateways and depending on what you want to achieve there is likely a gateway appliance involved in that architecture. And according to Microsoft this is how most of the customers are thinking about doing it.
According Microsoft research, people want to do this on a hybrid setting because they are simply not ready to go to the cloud and move all the users up there and trust a telephone company to help them. Nobody has ever done this what Microsoft is doing it with E5, specially at this scale.
Another tip: If you are familiar with ExpressRoute, customers can use it to connect their on premise to the cloud with a private connection keeping their current telephony carrier. As a matter of fact, this is the recommendation from Microsoft: Use ExpressRoute because you won’t rely on the public internet and, according to them, one will have more certainty and consistency in their telephony experience.
How Will the Billing System Work? How to Control Abuse/overuse of the Telephone Infrastructure with Office 365 E5?
Well, as of today, there are no over-usage charges as per-se in the new E5 plan. What is going to be put in place is monitoring of fraudulent behaviour and subsequent remediation. Let's say for example, someone left the telephone unattended for hours and hours and there is no audio. E5 will detect there is no voice coming through the endpoints so the call will be automatically disconnected. In that sense, it is expected there will be parameters that will monitor and manage and remediate issues/misuse when they occur, but MS at this stage did not signal any additional charges in the billion for over usage.
Also a cool thing if you live in the US is that the domestic service will be launched in the US with unlimited dial-in and out calls.
I love These Ideas. What Can I/We/My Company Do Now?
- If you or your company have access, deploy Skype for Business internally as soon as you can, then deploy the preview cloud PBX, PSTN conferencing and calling before the December 1st launch. Visit www.skypepreview.com for more info.
- Learns about Skype for Business Cloud Services. What Microsoft is doing here is an unprecedented move, from any cloud provider as a matter of fact, and with it a lot of new concepts, considerations and technologies comes into play. Now is the best time to learn about it and to position yourself as an early adopter on this growing market.
- If you’re a partner, start working on communications strategies to discuss opportunities on hybrid systems integration. A lot of people will be interested in learning more about it.
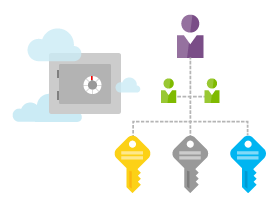
Customer Lockbox in the Office 365 E5 Plan
Every cloud service provider recognizes that your data in the cloud is yours and you want to have full control over its access . Customer Lockbox is a feature for Office 365 that provides customers with unprecedented control over their content in the service by giving them explicit control in the very rare instances when a Microsoft engineer may need access to resolve an issue.
The whole Customer Lockbox service has been engineered to require nearly zero interaction with customer content by Microsoft employees. Nearly all service operations performed by Microsoft are fully automated and the human involvement is highly controlled and abstracted away from customer content. As a result, only in rare cases a Microsoft engineer might have any reason to access customer data in Office 365, and when it does you, the customer, will be part of the process.
That technology, process and approval workflow is called Lockbox, and its approval process go through multiple levels of authorization. In addition, all access control activities in the service are logged and audited to make sure all compliance and regulatory needs are matched.
No other cloud service at this day offer this level of access and control where the customer can scrutinize the request and either approve or reject it.
A Matter of Trust
All this transparency and control are to make sure a satisfactory level of trust is maintained between Microsoft cloud services and the customers. All Customer Lockbox activity will be available to customers via the Office 365 Management Activity logs for easy integration into customer security monitoring and reporting systems.
The Office 365 E5 Plan
Microsoft announced a new E5 Office 365 plan and the E5 will contain that service by default. Customer Lockbox will be available for Exchange Online by the end of 2015, and for SharePoint Online by the first quarter of 2016.
Cyber Threats: Nation-States
This article is part of a series of called “Cyber Threats: Who Wants Your Money?”. If you missed the first post, you can read it here.
After the Operation Desert Storm, in 1998, USA for the first time has shown to the world their military prowess and how technologically advanced they were. Countries everywhere looked at how technology was being utilized by the US Marines and realized that simply no country was a match for them. The warfare landscape has been taken to a new level. The Chinese army were quick enough and studied how tech was applied by the USA and wrote a military study called “Unrestricted Warfare”. A classic now.
The summary of the book: A small nation can achieve a powerful hit against a bigger one by exploiting technological weaknesses. The technological warfare between nations started.
China then created a Cyber Militia, a group of hackers based on the findings of that study. Chinese schools invested heavily in programming and network computing. And I’ll use this Chinese event to explain a bit what goes behind the minds of a Nation-State Cyber Threat.
Why They Did it?
The answer to this question is similar to the answer “Why is Windows Phone trying to compete with iPhone?”. Because if they don’t, the competition will take over without resistance. And from a nation perspective, everyone was going to invest in cyber tech. China could not afford to be out.
Since then, reports of cyber attacks attributed as originating from China emerged in the news frequently.
What Is a Nation-State Attack?
Every western organization likely experienced an increase in port scans and access attempts to their systems around the year 2000. Port scans are considered attacks because they are done with:
- Explicit Intent to actively look for weaknesses in your security stance. These are not done for fun or curiosity, they carry a malicious purpose.
- Malicious Purpose. They are like “checking doorknobs on people’s houses”. Once they identify, the next step is to compromise information and integrity in exchange of political of financial gains
To mention a few examples:
- Google had been subjected to a sophisticated cyber attack
- Lockheed Martin, Dow Chemical, Coca-Cola and others all have been under cyber attack attributed to cyber nation attacks.
Regardless where they came from, executives all over the world recognized the threats and the Three Warfares was written. A mark on defensive systems against Nation-State attacks.
People started to understand their devices could be attacked, casual conversations recorded and personal storage devices compromised.
Small and medium companies started to be attacked. They were used as a new attack vector against their partners, big corporations.
Why Nations Do This?
Because it is profitable and offer an upper hand in tactical politics. Big damage can be done by small groups against large organizations by a fraction of the invested cost. According to Interpol data, cyber espionage theft amounts to US $1 trillion.
The Center for Strategic and International Studies, estimated that cyber espionage incurs in losses of about US $100 billion per year to the US economy.
Most of Countries are Capable of Cyber Attacks
A few countries are the undisputed leaders such as USA, Russia, UK and France. That’s where the power of alliances come into play, but many small nations proved to be highly effective. Take for example Stuxnet, which has the power to take over power grids and nuclear plants.
Have a look at this video explaining how powerful Stuxnet can be for a Nation-State attack:
It is impossible to talk about Nation-State attacks and not to mention Edward Snowden famous for the Wikileaks whistleblowing and now writing for the Guardian which “confirmed” the USA actually created Stuxnet.
Cyber Threats: Who Wants Your Money?
Nowadays, no organization which is planning to go or it is already (partially or completely) in the cloud can minimize the importance of cyber-security. Like a fighter during the last round of a combat, an organization cannot let the guard down after hours.
photo courtesy: @MSAU
Virtually everyone, from employees to executives and partners, are always connected to the Internet. Internet access is ubiquitous and everyone is carrying super-computers in their pockets.
And that increased surface of utilization created by the possibility of “access everywhere” challenges cyber-security status, because the interaction between smart devices and users and locations (safe or not) exposes individuals and companies to several security threats. That’s why in many organizations employees with access to important documents should treat their personal devices with the same rigor as their computing systems at work.
At the end of the day, cybersecurity is risk management, and the best approach to handle this is by establishing a secure corporate culture with positive management practices.
“Know Yourself and Your Enemy” – Sun Tzu
The internet is a fantastic place. Any information at the reach of your fingertips, however evil lurks. Cyber-Criminals are on the look out, looking for the right person to prey on. Day in, day out, thousands of hackers navigate through the web, attacking systems, devising plans, looking to exploit weaknesses in someone’s environment. 24x7. 7 days a week. The importance of the right security partner is paramount because it doesn’t matter how secure you try to be, hackers will always outnumber the defence team.
And now, hackers are not only after fame and glory. They are after intellectual damage and financial loss. Countries are fighting each other using the cyberspace, which created a whole new of threat classification in itself. It is like the wild west out there, and they are after everyone weak enough.
Despite that, successful enterprises didn't get there by avoiding risk. Instead they managed them to obtain a competitive edge on the competition.
The Enemy
The main cyber threats to organizations nowadays can be categorized as:
- Poor or Malicious Products
- Internal Threats (Insiders)
- Hacktivists
- Terror and Crime organizations
- Nation-States
Today we will start a series of posts targeted to “know your enemy”. We will identify the players in the current cyberwars, their threats and how to manage them.
Let’s start talking about the threats posed by Nation-States.
The World in the Year 2020, According to Gartner #GartnerSYM
Every year, Gartner releases a list of predictions in a huge simultaneous event across the globe (respecting the individual location timezones) which are followed closely by strategists, IT thought leaders, futurists et all from all over the world. The 2015 event key takeaways were:
- Autonomous Software,
- RoboBoss and
- Smart Devices.
I’ll spare you the suspense. Let’s go straight to them. Here are are Gartner’s top 10 predictions for 2020.
#10 - Writers Belong to the Past
Machines will be responsible for 20% of all business content created. In fact, these “robowriters”, as they are called, already produce reports, sports tickers, graphics etc. Once you stop to think about it, yeah, they are here already.
#9 - Connected “Things” will Need You
6 billion connected things will be requesting support. This “things” are smart-devices living in the Internet of Things (IoT) needing services, data etc. It is expected that campaigns of new business models will be developed targeting these “things” which will then influence their owners.
#8 - Software that Works on its Own
Autonomous software”, that’s the key. These are agents working independent of human interaction. They will participate in 5% of all financial transactions across the globe. Machine learning systems and predictive algorithms are actually beginning to perform transactions in many banks without our help as of now.
#7 - Meet Your New Boss: A Robot-Drone
3+ million workers will have a roboboss. It is unclear at this stage how this interaction will develop, as in a employee-boss setting or if it will be on a employee-watchdog basis. Either way, artificial intelligence will play a big part in this story.
#6 - RoboCop Buildings
20% of smart buildings will experience digital vandalism. From hacking to physical damage, these are smart, automated constructions which will affect the lives of communities around them. Hacking IoT is a new attack vector.
#5 - Top Companies will Have Machines as Employees
50% of the top IT companies will have more smart machines than smart employees. That’s because several smart machines will be easy to leverage new ones by the same group of smart employees.
#4 - Digital Assistants Will Interact with People
Digital assistants will finally recognize and interact with individuals by face and voice, a bit like what Microsoft Kinect does today. They will open the doors for a new age of biometric security, incorporated with a much powerful and consistent delivery.
#3 - All Your Health and Fitness Data Are Belong to Us
2 million people will be required to wear fitness tracking devices as a condition of employment. This will affect deeply the insurance industry and the design of smart cities. People will be encouraged to be healthier and with the “open doors privacy” (allowing iWatch, Facebook etc read and share individual data) currently being the status-quo, that trend will definitely get stronger.. Overall this is clearly a fantastic benefit for the community living in the year 2020. Likely people won’t be using independent trackers, but instead this tech will be incorporated into their current devices.
#2 - Apps will Use Apps for You Better Than You
40% of mobile interactions will be done paired with smart agents. Yet again another prediction following the mantra of autonomous apps and software.
#1 - When a Cloud Security Breach Happens, It is Because of You
Cloud security will be so powerful and so pervasive that 95% of all failures happening in the cloud will be due to customer's fault (not the vendor’s), varying from poor usage and risky user behaviours up to incompetence. Did your data leaked to 4Chan? Don’t blame AWS or Microsoft. It was you!
Personality and Imperative Test: Ambassador
I’m not a big fan of personality tests. I think that sometimes they show a different side of us that might not represent our individual as a whole. However I took the suggestion of a friend over twitter and gave the www.imperative.com a try. And I was pleasantly surprised. The description is very very accurate about my drivers in life.
I am not sure if you believe these things or not, either way give it a try. Worst case scenario it will be fun.
Meanwhile have a look at my profile. Below are my results:
The Ambassador
You make your mark on society by facilitating authentic human connection.
You change the world by connecting and bringing people together. Driven to promote fairness and equality to ensure equal access to opportunities - you work to empower communities and enable them to tackle significant challenges that bring about large-scale change. By connecting people through a shared vision and fostering commitment and ownership, you ignite the collective energy and drive needed to move towards concrete societal progress. Your work feels especially worthwhile when you see your contributions leading to widespread changes that expand opportunities for all.
Who Do I Want to Impact: Society
You seek to impact communities and society. You find purpose when you:
- See others promote your solutions and ideas
- Implement a new policy
- See a change you made have long term impact
Why Do I Work: Harmony
You are driven to ensure everyone has access to opportunity. You find purpose when you:
- Level the playing field
- Help others overcome barriers
- Ensure everyone is heard
How Do I Solve Problems: Community
You bring groups together to build engagement and ownership. You find purpose when you:
- See a team come together to accomplish a goal
- Connect two people who would get along
- Empower a group solve its own problems